Who we serve
DEFENSE
In Today’s always changing world, we help military forces around the world to get the job done efficiently. Nowadays, the way we protect our borders from enemies has dramatically changed. To win and keep our territory protected, the new military forces require top technology. Rational Point provides the best solutions for today Defense communications, Intell & Counter-Intell, border protection and cyberwar tools.
Solutions:
- 4G-5G communication networks.
- Tactical communication solutions for immediate deployment.
- Cyber-security tools.
- Rugged phones and tablets.
- Border control solutions, including aerial surveillance, land and sea sensors.
- Intell & Counter-Intell solutions.
- APCs.
-
Aerial surveillance, Drone Detection, Identification, Tracking and Denial.


LAW ENFORCEMENT
Rational Point provides the most modern and efficient tools to help Law Enforcement institutions around the planet, to enforce the law by discovering, deterring and rehabilitating people who violate the rules and norms governing that society.
Solutions
:
- Secured Communications
- Intell & Counter-Intelligence solutions
- Investigation tools
- Cyber security solutions and services
- Video analytics and facial recognition
- rugged communication devices
- Special vehicles and APCs
-
Aerial surveillance, Drone Detection, Identification, Tracking and Denial
GOVERNMENT
Today’s Governments face new challenges. Smart cities, reduced budgets, saturated and overpopulated urban areas, under-served rural populations, illegal immigration, changing labor market, globalization… We can help. Rational Point has the experience to design Ad Hoc solutions for almost every problem related with security or cyber security.
Solutions :

- Public Safety and First Responders Ad Hoc Solutions.
- Secured Communications; Counterintelligence solutions.
- Cyber security solutions and services.
- Video analytics and facial recognition.
- Rugged communication devices.
- Epidemic Monitoring & Control Systems.
- Special vehicles
- Risk assessment, Red Team and Penetration test
- Counter espionage measures
- Check for cellphone and computers’ malware
- Check for concealed cameras and microphones (home, office, car)
- Physical security solutions
- Forensic investigations after cyber attack (identify damages and the attacker)
- Evidence collection and analysis
- Analysis of interests and conflicts
- Identifying misconduct and fraud investigations
- Individual, entity and assets tracing
- Economic investigations
- Loss prevention
- Computer crime investigations and digital forensics
- Tracing dormant accounts

PORTS AND AIRPORTS
Ports and airports are the most used entrance and exit to a State or Nation. Meaning that terrorist, spies, drug dealers, justice fugitives, illegal aliens, smugglers of any kind use them everyday. Rational Point can help to improve monitoring, detecting and controlling these strategic areas more efficiently, saving time, money and human resources.
Solutions :
- Scanners and substance detectors.
- Drones denial systems.
- Intrusion detection & access control.
- Video analytics and facial recognition.
- Risk assessment and gap analysis
- Consulting
- Operational engineering
- Training
- Wargames simulations
- Security Solutions
- Transportation security (ground, maritime and aerial
- CCTV command and control design and operating
-
Aerial surveillance, Drone Detection, Identification, Tracking and Denial.
PENITENTIARY CENTERS
As the popularity and benefits of wireless communications grow, so do unwanted side effects – such as use of cellular devices in restricted areas. Recent national security events ranging from illegal activity coordinated from correctional institutions to information and security leaks from secured facilities have only emphasized the need to implement a measure of communications control in these targeted areas. Leveraging the patented technology of Managed Access as well as multi-protocol wireless operations, the Intelligent Network Access Controller (iNAC)TM, forms a radio frequency umbrella around a precisely defined target area and manages cellular devices within range. iNAC Managed Access provides the system operator with the capability to selectively permit or deny communications for devices within the restricted area based on a rich policy engine that includes continued support for cellular network regulations such as 911. The iNAC does not require changes in law to operate.

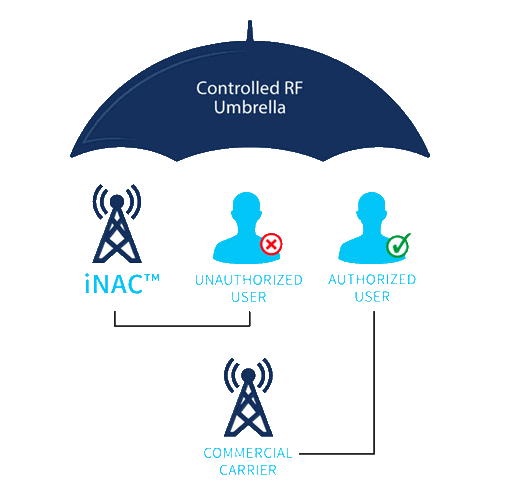
Solutions:
- Communication Security & Intelligence.
- Illegal phones detection and blocking.
- electronic bracelets.
- Video analytics and facial recognition.
- Drone detection and denial systems.
CORPORATIONS
Globalisation has changed the structure and pace of corporate life; the saturation of traditional markets pushes company to take more risks; the shift towards a knowledge economy is eroding the importance of ‘place’ in the business world; new business practices such as offshoring challenge companies to manage at a distance. At the same time, security risks have become more complex, too. Many of the threats, such as terrorism, organised crime and information security, are asymmetric and networked, making them more difficult to manage. There is also greater appreciation of the interdependence between a companies and the way they do business. As a result, security has a higher profile in the corporate world today than it did ten years ago. Companies are looking for new ways to manage these risks and the portfolio of the security department has widened to include shared responsibility for things such as reputation, corporate governance and regulation, corporate social responsibility and information assurance. Rational Point has the expertise and solutions to help today corporations to stay ahead of the competition, while keeping their physical, digital and intangible asset safe.
Solutions :

-
Cyber-security
-
Intrusion Control & Access Control
-
Secure Communications
-
Scanners and substance detectors
-
Forensic investigations after cyber attack (identify damages and the attacker)
-
Physical security solutions
-
Evidence collection and analysis
-
Analysis of interests and conflicts
-
Identifying misconduct and fraud investigations
-
Individual, entity and assets tracing
-
Economic investigations
-
Check for concealed cameras and microphones (home, office, car)
-
Loss prevention
-
Computer crime investigations and digital forensics
-
Tracing dormant accounts
-
Transportation security (ground, maritime and aerial)
-
CCTV command and control design and operating
-
Intelligence research and analysis
-
Open-source collection and analysis
-
Industrial Counterespionage
