Smart Solutions
For a Better World
Secure Communications
Rational Point multi-technology NIB solutions provide easy-to-use, deployable communications, addressing the need for mission critical, turnkey network coverage in the field. The high- speed bandwidth, robust capability set, compact form factor, and cost-effectiveness of our’s NIB product line enables a broad range of deployment scenarios for remote and rural locations, defense, security forces, public safety and peacekeeping missions in addition to mobile communication networks in transit.
RATIONAL POINT’s robust hardware and software solutions have easily integrated into military platforms and defense communications system for the warfighter through network-centric operations. Our partner, Tecore Networks, has worked on many U.S. Government programs with large and small integrators, creating secure mobile communications solutions. Our multi-technology software defined core network is scalable to meet any mobile infrastructure requirement.
Our Solutions
- Ad Hoc Secure Communication Networks.
- Tactical Networks for immediate deployment.
- Secure phone communications (voice, messaging and attachments).
- Communications security and intelligence for critical infrastructure

When the industry ushers in the next generation of wireless, we will be there with a comprehensive upgrade continuing their proven product evolution path across multiple generations and technologies. As today’s government and military infrastructures are moving to incorporate commercial wireless technology into their communications backbone, Rational Point will continue providing secure, reliable communications.

Cyber Security
Extending the Protection Chain Across Multiple Perimeters.
In recent years, the distributed nature of computing resources and the ubiquity of mobile devices has led to porous network boundaries and more opportunities to exploit weaknesses in perimeter defenses. Security technology and solution providers continue to place an outdated emphasis on the perimeter, instead of focusing security efforts down to a more granular scale and protecting what is actually valuable – sensitive data itself.
Furthermore, with Today wide use of mobile phones, the risk of being attacked and exposing you private and corporate data has skyrocketed.
Our Solutions
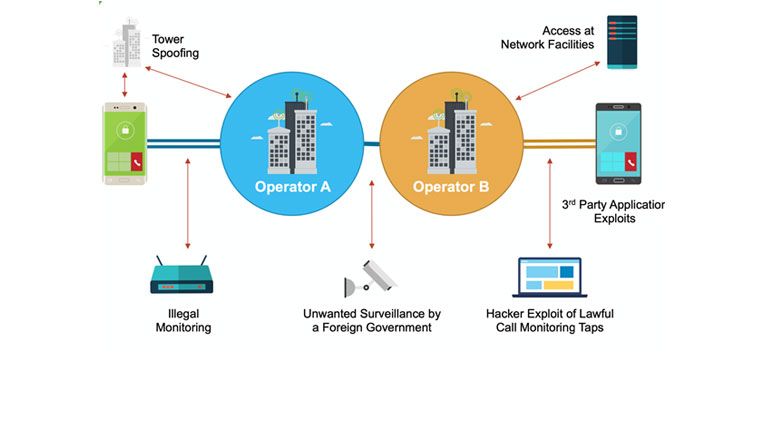
- Attacks grow in volume and sophistication. Intercepting a phone call or text message is very easy. Nowadays, with very little money, anyone can buy an internet interception team.
- State espionage is a serious problem with disastrous consequences.
- Every day the media informs us about new scandals of politicians, businessmen who have been recorded during apparently private and secure telephone conversations.
- Criminal networks have easily intercepted police communications throughout the region.
- Industrial espionage uses telephone interception as their favorite tool to gather information about competitors.
- Malware has generated billion of dollars in financial loss for thousands of companies around the world.

 SIEM SOC as a Service Solution
SIEM SOC as a Service Solution
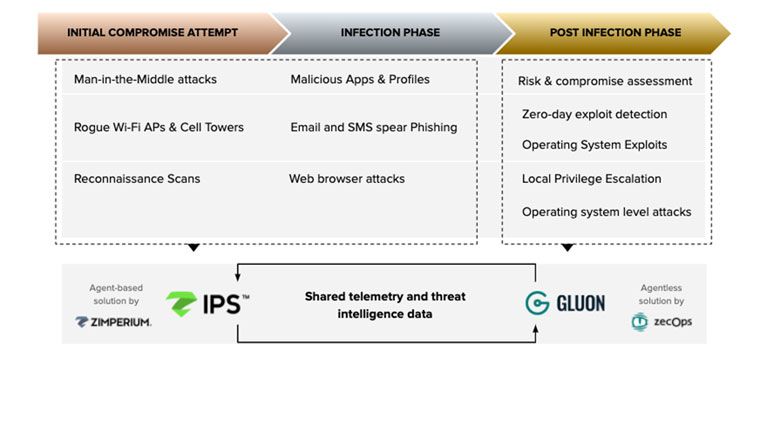
Today is almost impossible to find the adequate personnel required to keep corporations and institutions around the World safe from cyber-attacks. There is an intense competition to hire the cybersecurity experts needed to protect their digital assets. The vast majority must content with what they can find, which is generally not what they really need. Not anymore! At Rational Point we have gathered the best cyber security experts from Israel and USA in one SOC, 24x7x365, to protect companies and government institutions around the globe in a very effective and cost-efficient way. Our SOC +SIEM remote services is our core engine for our CSaaS (Cyber Security as a Service)
SIEM System:
-
Working with the leading products in the SIEM market (Gartner)
-
Ability to Parse hundreds of products (out of the box and manually by our team!)
-
Support for OT system
SOC Operations:
-
SOC Leaders
-
SOC Operation Methodology
-
Integration with 3rd part tools to expedite and provide insights for SOC Operation
-
Analysts Training program
-
Continues Risk Assessment
Incident Response Team
-
Detection - Gathering information from the SIEM & Cyber Intelligence sources.
-
Using dedicated investigation environment with multiple 3rd party tools
-
Full incident management, investigation, mitigation and recommendation for recovery
 Cyber Consulting
Cyber Consulting
Our consulting unit offers a full menu of cyber security professional services, including:
Ofensive Team
-
Ofensive Team
-
Mobile Application Penetration Testing: IOS / Android
-
Web Application Penetration Testing: Black/Grey/White Box
-
Network & Infrastructure Penetration Testing: Black/Grey/White Box
-
Red Team Services
-
Social Engineering
-
Cyber Attack Simulations
-
Hackathons \ CTF
Defensive Team
-
Incident Response
-
Regulatory Compliance and standards
-
Secure design of information systems and architecture
-
Technology and devices configuration reviews
-
Organization Secure Architecture
-
Secure code review
-
SOC Methodology review
-
Risk Assessment
-
Information security policy and procedures
-
Hardening and defense settings documentation
-
Business Continuity Management. Disaster Recovery Planning & Review
 Products
Products
-
BITDAM: BitDam is a pioneer in cyber defense that safeguards email and collaboration tools from advanced threats including ransomware, phishing, BEC and more. Leveraging its patented knowledge-independent technology, BitDam is the only vendor to stop unknown threats at first encounter before other security solutions identify them. The company’s cloud-native solution, BitDam ATP+, offers complete security against attacks of any type across O365 email and other business collaboration tools. Named a 2020 Gartner Cool Vendor in Cloud Office Security, BitDam’s solution is utilized by organizations worldwide with a proven record of detecting threats that others fail to uncover.
-
ACRETO: Acreto is SASE+ Plus (Secure Access Service Edge). SASE+Plus is a cloud infrastructure that connects and protects all your technologies with a single, simple service. It goes beyond secure application access to provide end-to-end connectivity and security for any technology, any network, anywhere
-
FORNETIX: The Key to Data Security. VaultCore is the leading product from Fornetix and it was built to make encryption of data seamless, rapid, flexible, scalable, and budget friendly. We connect with leading technologies around the globe to automate and orchestrate encryption on a massive scale. Simple, centralized control of security and access policies prevent human error, reduce operating costs, safeguard critical data, and ensure regulatory compliance.
-
ZECOPS: ZecOps for Mobile is the only available tool that provides the capability to extract, deliver, and analyze the mobile device logs for signs of compromise or malicious activity."
-
KELA: The Global Leader in Actionable Threat Intelligence. Kela delivers the world’s best intelligence solutions that empower organizations to neutralize their most relevant threats observed in the cybercrime underground ecosystem. Kela are the world leaders in DarkWeb/Deep Web investigation tools and services.
 Training
Training
With an increasingly digital world and surges in cybercrime, there is a huge deficit of cybersecurity professionals. This has become a worldwide problem. Rational Point has built alliances with Cybersecurity Education Institutions in Israel and USA to bring innovative learning methodologies to governments and corporations in the Americas. Contact us to learn more about our remote courses and certifications.
Security
Check for concealed cameras and microphones (home, office, car)
Physical security
solutions
Evidence collection and analysis
Homeland and national security
VIP personal
security.
C5ISR.
Special units
training
Tracking
Physical security (infrastructure and buildings)
Transportation security (ground, maritime and aerial)

Surveillance and Intrusion Detection
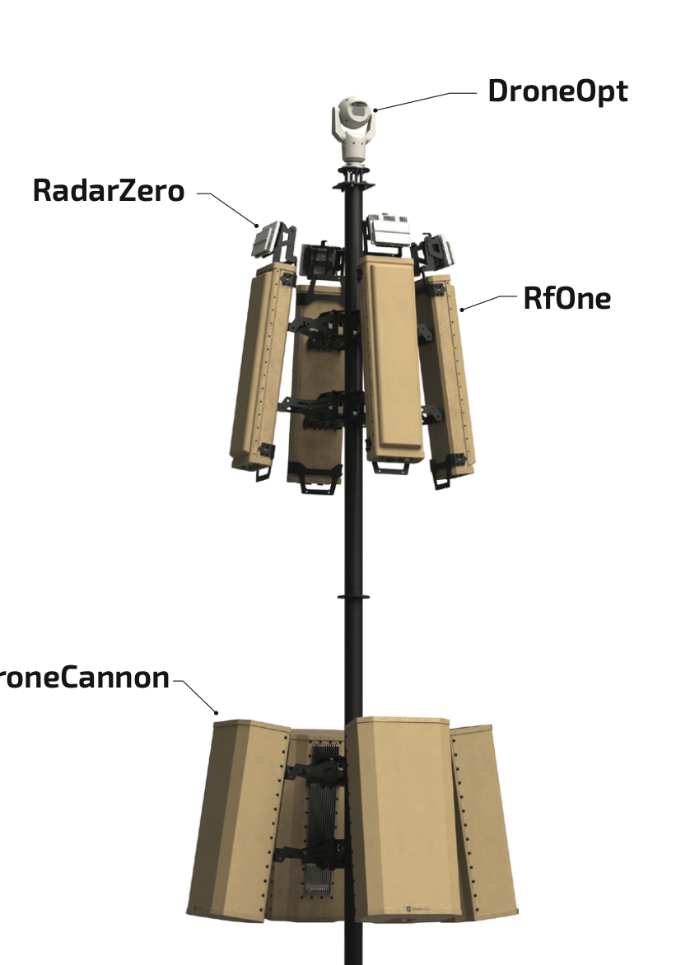
We listen to our customer, we understand his problem. We work with him to design a specific solution to solve its problem. We have all the tools required for the job. If we don’t, we will find it.
Rational Point has the broadest range of products in the perimeter security marketand provides flexibility, choice and multiple layers of security if required.
Our Solutions
-
Border control and intrusion detection.
-
Surveillance and perimeter control.
-
Asset tracking and access control.
-
Criminal networks have easily intercepted police communications throughout the region.
-
Video analytics and facial recognition
-
Aerial surveillance, Drone Detection, Identification, Tracking and Denial.

Intelligence
With more than 25 years of expertise in the industry, Rational Point offers a range of solutions helping governments to address todays’ homeland security challenges. Rational point provides law enforcement and intelligence agencies with a comprehensive portfolio of premium, best of breed intelligence solutions, integrated to enable unique synergetic functionality :
- Field Intelligence
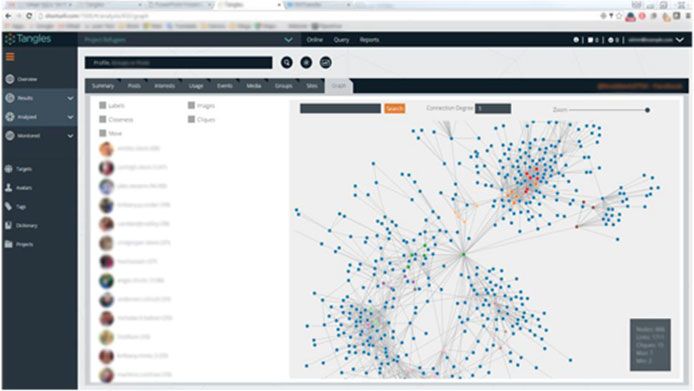
We offers a variety of solutions for the field intelligence teams that enable maximal operational flexibility while minimizing the risk of exposure . Our comprehensive solutions empower the field operation teams , with a wide variety of field and cyber collection systems as well as powerful analytics capabilities and local access to strategic intelligence.
The solution supports the entire field intelligence process – detection, location, interception, infection and analytics.
- Network Intelligence
We offers a variety of network intelligence solutions that enable covert mass collection and analysis of data from a variety of sources – network switches, SS7, and open sources.
To be successful your content needs to be useful to your readers.
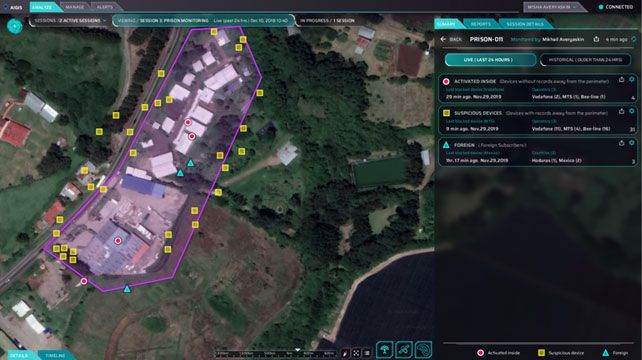
Our Solutions
- Investigation tools
- OSINT
- 2/3/4G Intelligence & Locations Systems
- Wi-Fi Intelligence Systems
- Interception Systems
- Mobile Network Forensics
- Mobile Network Counter Surveillance Security
Counter-Intelligent
Spies and terrorists might seem like a throwback to earlier days of world wars and cold wars, but they are more prolific than ever—and they are targeting the nation’s most valuable secrets. The threat is not just the more traditional spies passing our secrets to foreign governments, either to make money or advance their ideological agendas. It is also students and scientists and plenty of others stealing the valuable trade secrets of universities and businesses—the ingenuity that drives our economy—and providing them to other countries. It is nefarious actors sending controlled technologies overseas that help build bombs and weapons of mass destruction designed to hurt and kill us and others. And because much of today’s spying is accomplished by data theft from computer networks, espionage is quickly becoming cyber-based.
Source : The Federal Bureau of Investigation (FBI).
Our Solutions
- Cellular Boarder Safety
- Secure Site Creation
- IMSI Grabber Detection
- SS7 Firewall Protection
- Virus, malware device scanning
- Jammers
- Bug detectors
- Drone detection & denial systems
- Mine detectors
Special Vehicles
To provide our customers with the best armored vehicles in the market, Rational Point partners with INKAS.
INKAS® Armored Vehicle Manufacturing is a leading Canadian-based company that specializes in the design and production of a wide range of armored vehicles, including executive SUVs, bulletproof luxury sedans, special purpose vehicles, personnel carriers, cash-in-transit vehicles, and others. Since 2000, INKAS® Armored Vehicle Manufacturing has been providing armored vehicles for banks, law enforcement agencies, corporate clients and individuals all over the world. Company’s worldwide sales offices and after-sale workshops are located all over the world.
To address the threats our customers face all over the world, INKAS® Armored Vehicle Manufacturing implements the best practices in technological innovation, design and quality management. Our armored vehicles ensure your security and protection.

AUTONOMOUS DRONE-IN-A-BOX SOLUTIONS
Military-Grade Surveillance, Monitoring, & Inspections
Going above and beyond available systems on the market, Easy Aerial's solutions are engineered to meet the widest variety of operational requirements.
Available in three configurations - tethered, free-flight (untethered), and the industry’s first tethered/free-flight hybrid configuration, each of our portable drone-in-a-box solutions can be customized to meet any security, mapping, and inspection needs.
Developed and proudly built in the U.S, Easy Aerial’s durable, cost- effective solutions have proven operational experience – even in the most demanding environments. They can be automatically deployed and commanded remotely from any location worldwide and can take off and land from a moving platform, such as a ground vehicle or watercraft.
Whether conducting perimeter patrols or securing a border, monitoring a crowd or inspecting critical infrastructure, Easy Aerial provides a reliable eye in the sky for mission-critical operations.
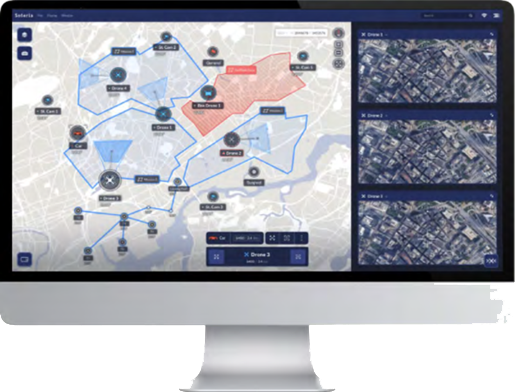
Easy Aerial offers the most robust and versatile autonomous airborne security, monitoring, and inspection solutions on the market today.